In a post I wrote a while ago, I explained how to create a SharePoint custom permission level and special SharePoint groups to be used in Power Apps using PnP PowerShell. And also how to break the permissions on the specified site lists while granting access to the new groups only to those lists. Then, the users from those groups would be able to access the lists only from the app interface and not from the SharePoint UI.
If they tried to open it from the SharePoint interface they would get an access denied message:
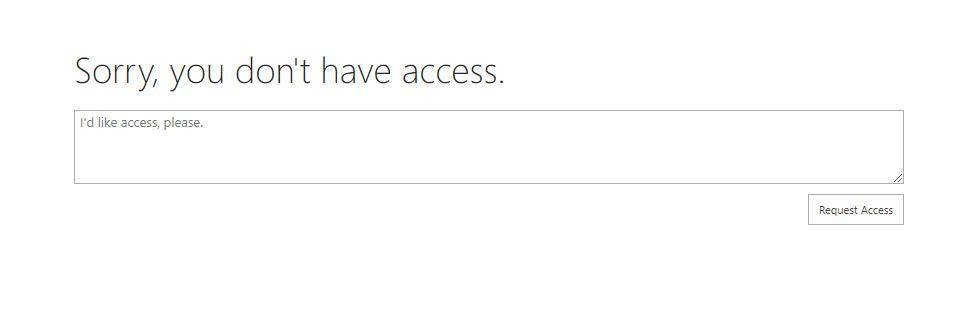
This scenario was ideal in case a SharePoint site was used to host the app lists, and more information that might be used by other people from SharePoint, so you would restrict only access to specific lists and not the full site.
Restricting the full site
There are cases where a SharePoint site is used only as a container for lists to be used in a Power App, so it will make more sense to not break permissions in the list, and instead to simply change the permission levels for the site members on the site directly.
Some people have asked me if we can do the same configuration from the SharePoint UI, and also if it was possible to limit access to the full SharePoint site.
Enable Limited-access user permission lockdown mode
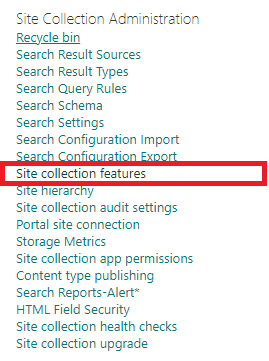
For the trick to work we need to enable the ‘Limited-access user permission lockdown mode’ under the site collection features:

Custom Permission level
Consider a Power App connected to a SharePoint site where you would grant access to people using the members group. For this case, we can reuse the same group, but we need to change the permission level to a custom one.
First of all, we need to create a custom permission level.
Note: The steps below will work for Classic Sites, Communication Sites and Team Sites that are not connected to Office 365 groups.
To begin, navigate to the Site Contents page:
Open the Site Settings page:
Then navigate to the Site Permissions page:

And select permission levels:
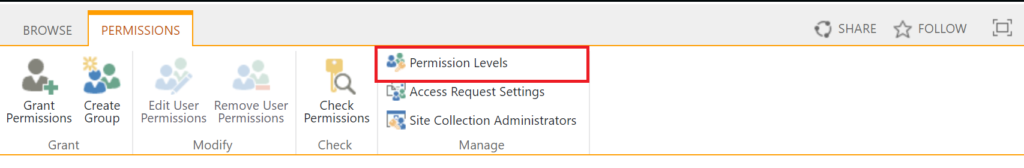
On the Permission Levels page, select the Contribute permission level:
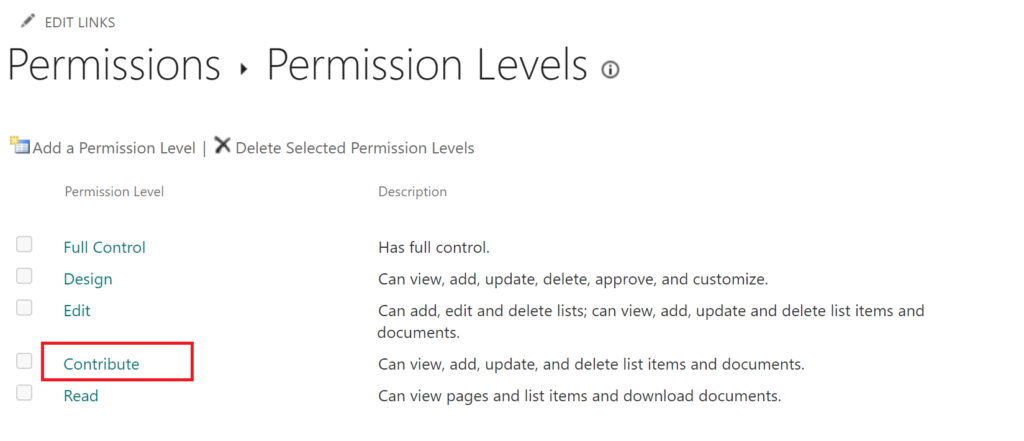
On the permission level settings page, don’t change anything.
Instead, scroll to the bottom and click Copy Permission Level, so a copy of the Contribute permission level will be created. We then tweak this copy instead of the default Contribute permission level.
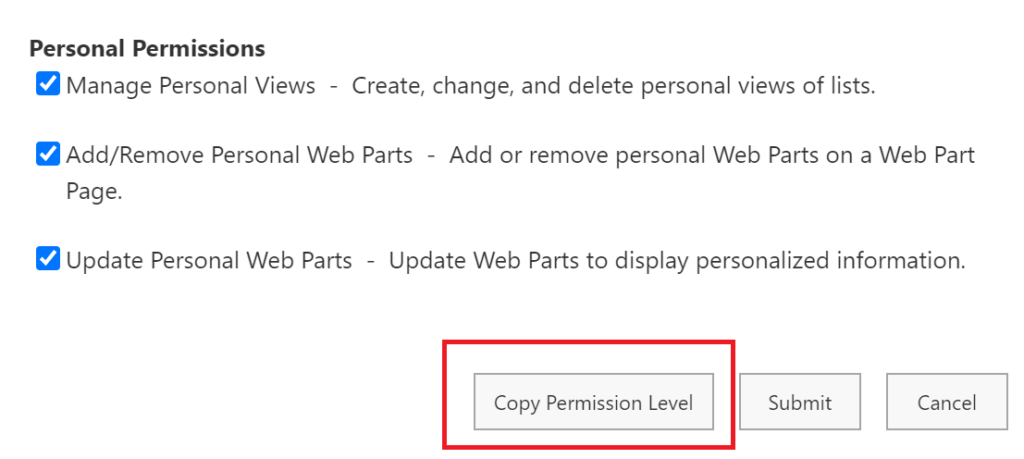
On the Copy Permission Level Page, give your new permission level a suggestive name such as Contribute From PowerApps.
Unselect the permission option View Application Pages. This is the option that would grant the user the rights to see the data from the SharePoint pages/interface.
Save your changes to create the new permission level.
Changing the site Members’ permissions to the ‘Collaborate from Power Apps’
Back to the Site Permissions page, select the Site Members group and edit its permissions:
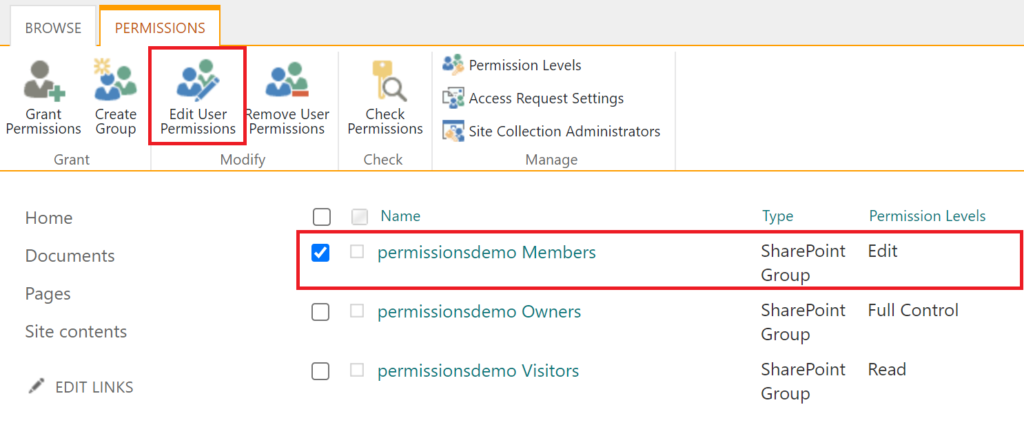
Unselect Edit or any other level in case you had changed it previously, and select the new permission level:
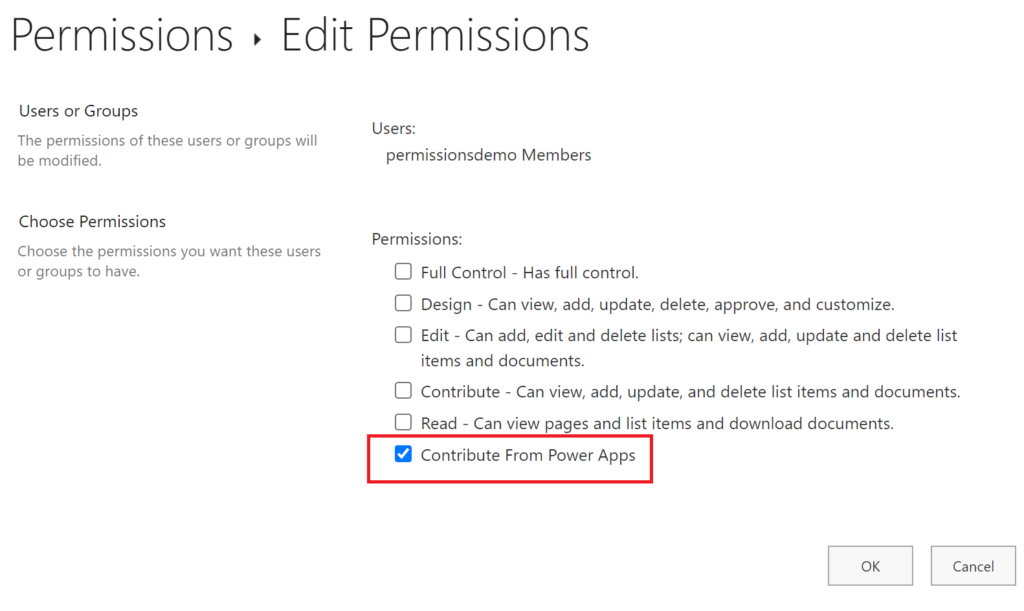
After confirming, the new level is applied:
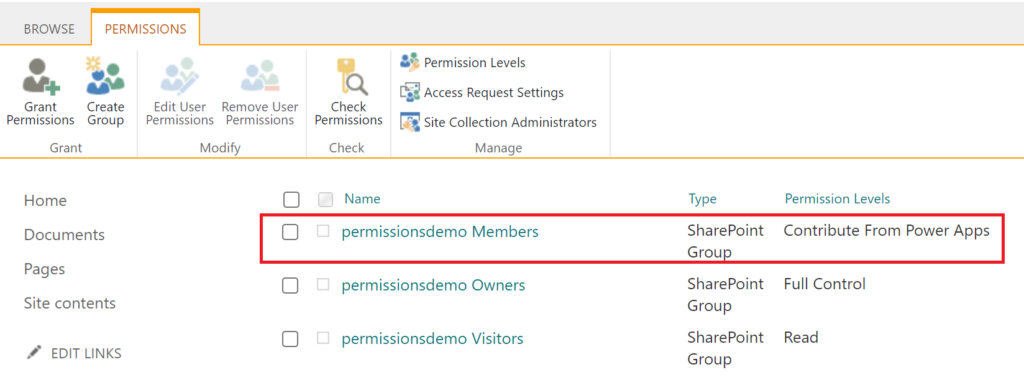
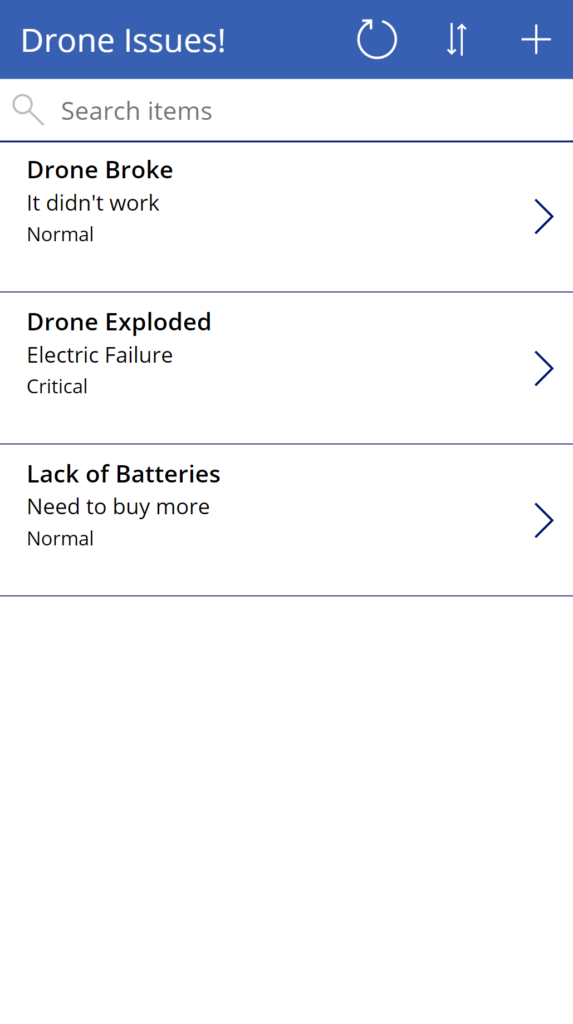
Results
When a user that is not a site owner, and has access to the app data only from the new permission level opens an app that uses lists from a site with the above setup, the results are normally displayed:
But when trying to open any list or the root site from the browser, they will get an access denied message:

Now your app users won’t be able to bypass the app rules and interface by accessing data directly on SharePoint.
Additional notes: As a good practice and to make your life easier, you can create an Azure AD/Microsoft 365 security group to manage security on the site and the app at the same time. Use this group do add all app/site users. Then you add this security group to the members group on your site, and share the Power App with the group. For new users added, you simply would need to add them to the security group only and they get the right permissions (otherwise there are two pieces to be always managed, one from SharePoint and the other from Power Apps).
Also bear in mind that this approach blocks the users from opening items from the SharePoint UI, but in the same way, they can access data from your apps, if they are smart enough and find the site URL they will be able to bypass your app’s rules/permissions by creating another app connecting to those lists or using the SharePoint APIs in any way. So if you are looking at blocking it even in that way, additional treatment would be needed such as item/folder level permissions to prevent items to be viewed and/or Remote Event Receivers to implement rules when saving data.

[…] Steps to deny Power Apps users access to SharePoint data from the SharePoint UI – michelcarlo […]
Would this be the part that I go – Doh!…… Should have thought of that….lol
Good solution.
HAHAHA
Thanks ,Maurice 😊
Superb!
Just one query.. you have stated that
“The steps below will work for Classic Sites, Communication Sites and Team Sites that are not connected to Office 365 groups.”
little confused about this. I am using Microsoft lists . Have created permission level on site as mentioned above and then applied it via setting in “Microsoft Lists” will that work
Hi Majesh, if you selected a Communication or Modern Team site to create your list when creating it from Microsoft Lists it will.
I want to thank you, I have come across MANY places that indicate this is not really possible. The other plausible solutions I found were not remotely as elegant or scalable. My main issue with PowerApps configured with SharePoint was the off chance someone might find the list behind the scenes. ListItem level permissions did not feel scalable for the work I was doing. I also appreciate the fact that you highlight the API consideration, something I am not concerned about with the user base I am securing my app for. Thank you!
No worries, Boe. Another point to highlight is the people would be able to create a power app and connect to the list if they know the site address…but this approach makes harder anyway as they wouldn’t know it from accessing it from SharePoint.
Hi
Thanks for your advise. Our problem don’t solve yet. Because we will use desktop to connect powerapps application. So we add short cut on sharepoin site to connect applications. When we uncheck “View application pages” also powerapps applications don’t open too. Please give you advace if you have a solution. Thanks.
Hi,
Are you using a Power Apps custom form in a SharePoint list or a Standalone Canvas app?
Hi,
Thaks for your return.
We use Standalone Canvas app but we are connecting apps from the sharepoint. So we added short cut on the sharepoint browser like “Company Applications” folder to connect powerapps apps. So if we unselect “view application pages”, short cut for “Company Applications” and also Documents don’t seen on the browser.
Note: We added 5 powerapps application link on Company Application folder. We will connect to applicatons from this links.
If you have any advise let me know.
Thanks
Ideally you would store the lists for those apps in a separate SharePoint site. Then you remove the View Application pages permission from the users only from the lists/sites used to store data.
And you allow the users to navigate to your Canvas apps from a second site, in which they have normal access to pages.
Nice approach!
I’ve handled this in the past by renaming the “home.aspx” page to something like “NoHome.aspx”, creating another page with links to the lists and to the Site Contents, and giving the link to the new page to those who needed/wanted to access the SharePoint lists directly from the site.
This seems to be a much more elegant solution – thanks!
Thanks for the feedback! 😁
You approach was a creative one, however bear in mind the users could open the lists if they know the direct link to them…
Hi,
This approach doesn’t seem to stop users been able to view the list in the browser by going to the URL directly. I don’t think I’m doing anything wrong.
I think it may have something to do with the ‘site permission’ “View pages” been ticked. I cannot untick this as it’s automatically ticked when I select the ‘list permissions’ “Add items”.
https://docs.microsoft.com/en-us/sharepoint/sites/user-permissions-and-permission-levels#site-permissions
Any ideas on why this isn’t working? We are using SharePoint Online.
Thanks
Hi Danny,
I have just checked this and it seems you are right. Something must have changed in SharePoint and depending on how the users tried to access the data they would be able to.
Two approaches are still valid:
1) Use the content from this post and also enable the ‘Limited-access user permission lockdown mode’ under the Site Collection Features.
2) Don’t grant the access on the site directly but break permissions in the list, and grant the user/group permissions using the custom level without ‘View Application Pages’ .
Let me know how that goes.
Thanks man!
Would this make it so they could still view the power app in a SharePoint web part? Or would they have to use a direct link to the app?
If the WebPart is placed on another site, they will be able to see the content. The goal here is to force the users to use any Power App to load the content, instead of navigating to the site where the lists are.
If you build an app that reads data from site X and then put it on a WebPart in site Y it will work.
[…] the list directly through the URL in their browsers. Allowing them to do so could potentially disrupt the functionality of the Power Canvas app by creating or modifying […]